Every network engineer has at some point in their career have had to deal with the problem of overlapping CIDRs. Classically these problems have been solved at the routing layer using VRFs, tunneling etc. However with the center of gravity moving to the cloud, there is an opportunity to adopt a horses-for-courses approach instead of a one-size-fits-all approach that ties customers down to an L3-heavy architecture.
Where the Problem of Overlapping starts..
It is helpful to understand the context in which these class of problems occur and therefore adopt a pragmatic and cloud-native approach to solving these problems in the hybrid-multi-cloud context.
There are some broad business initiatives that typically lead to this class of problems in the networking and connectivity layer.
- B2B or partner exchanges.
- Shared services that need to be accessed by different accounts.
- Mergers and acquisitions
- Overlapping by design ( BU/org level allocation of CIDRs in different accounts)
Diving a little bit deeper into these use cases is crucial in order to determine the best connectivity approach.
B2B exchange
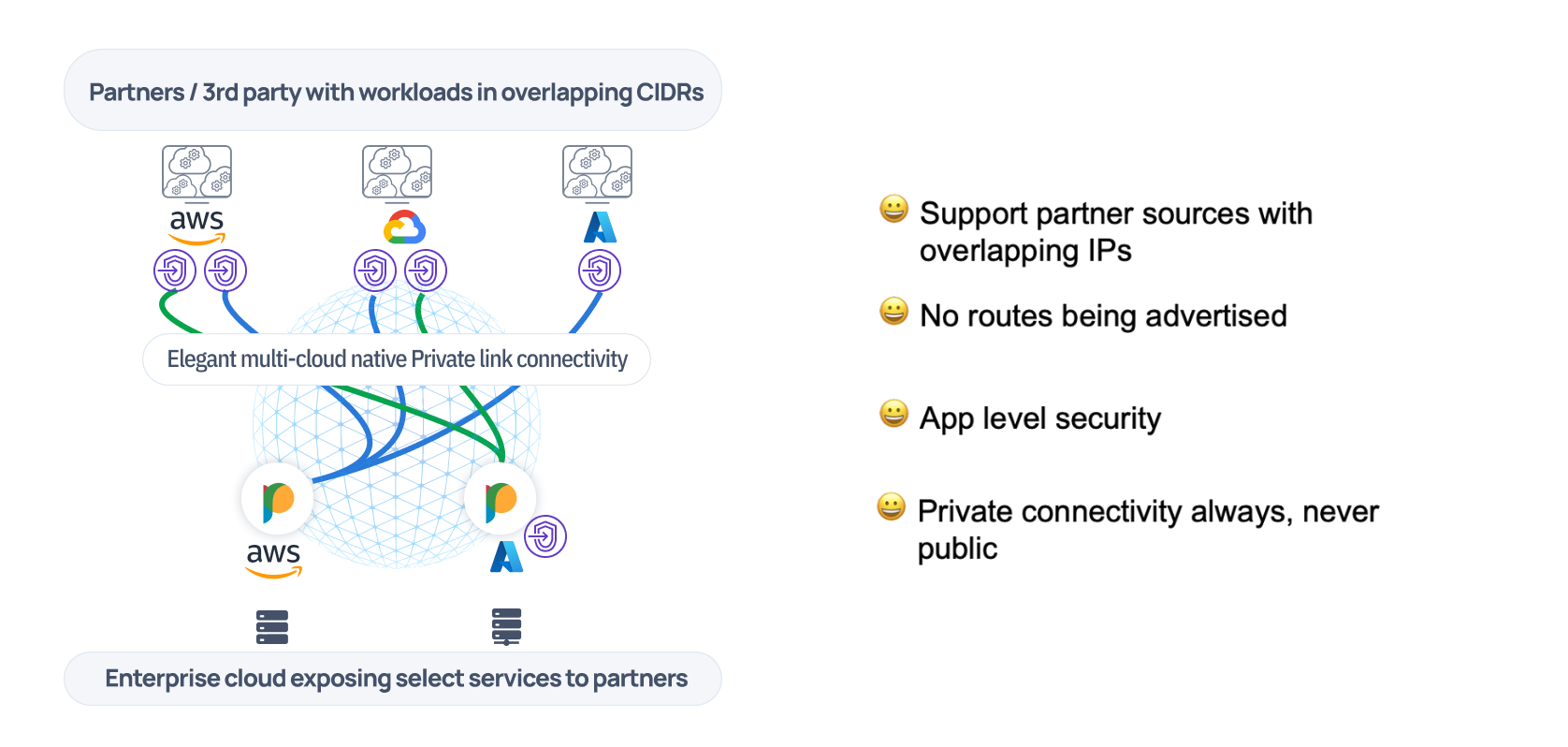
Several customers have asked us for a solution where partners or third party service providers need access to applications or databases in the core network.
There is no control over the CIDR ranges of these partner sources or even cloud venues. A partner could be running these source workloads in CIDR A in AWS and another could be using an overlapping CIDR in Azure. Both these partners need to access a database in the enterprise account. Now a layer 3 solution would mean learning and advertising these routes into the enterprise core ( a security problem) and then dealing with routing these overlapping CIDRs ( a connectivity problem). Moreover, an enterprise would have a hard time asking partners to either change their CIDRs or run appliances in their cloud accounts with the added complexity of managing their lifecycle over time.
The desired outcome is to selectively connect these applications or services to these partner accounts without having to deal with the networking complexity underneath.
This is where being cloud-fluent and cloud-native helps. Prosimo Private link sources provide an easy way to connect these core applications to the multi-cloud partner accounts while securing access through a rich policy engine. No routes being advertised or security being compromised.
Partner/B2B exchange with Prosimo Private Link Sources
Shared services or Dynamic PaaS services
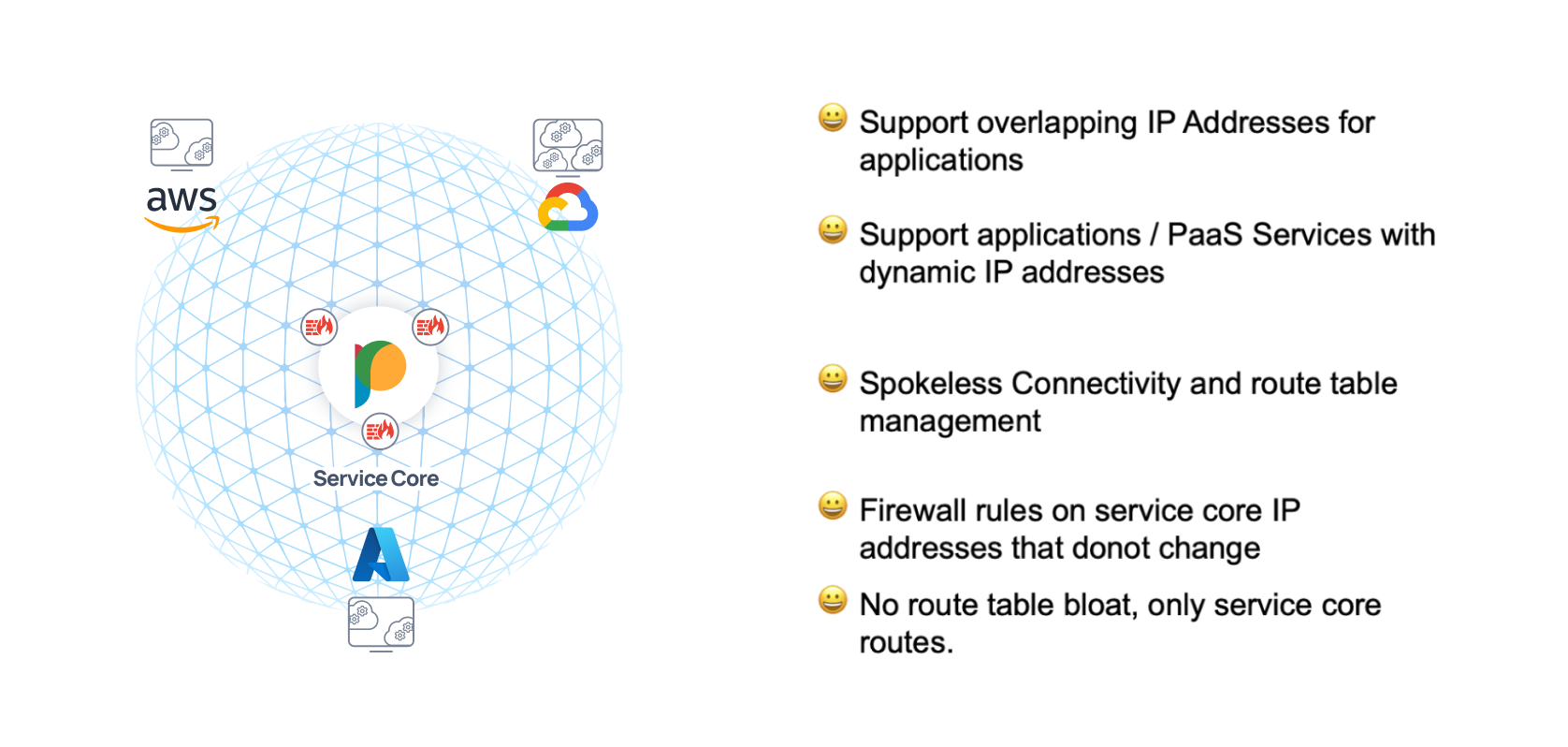
Another common class of problems is accessing shared services from different accounts. An analytics workload trying to access data from HR and Finance databases possibly across different accounts. The problem is even more complex when the shared service is a PaaS service or front-ended by a load-balancer that keeps changing IPs. Using VRFs to segment these workloads and selectively leaking them or using NAT-ed subnets leads to unnecessary overhead in terms of appliances or route table bloat.
Again being cloud native and solving these challenges in a cloud native manner allows us to use an approach that works for both these scenarios. With Prosimo Service core, customers are able to access applications with unique IP addresses that the Prosimo transit provides throughout the multi-cloud fabric. Relying on a combination of private DNS resolution to these service core IPs and the Prosimo transit routing these requests to the right application endpoints by dynamically resolving them, we are able to handle both these cases without needing any additional appliances or configuration and management overhead for our customers.
Prosimo Service Core
Applications with Dynamic / Overlapping IPs
Mergers and acquisitions
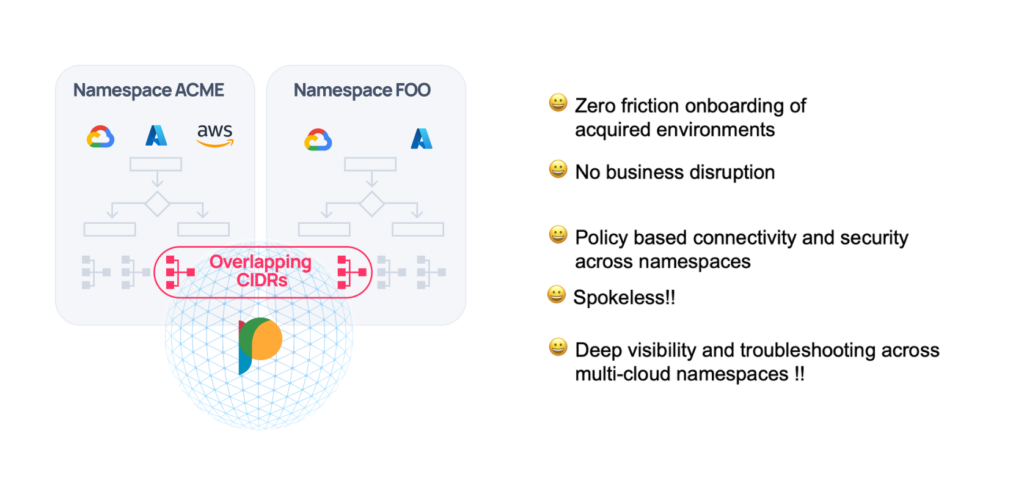
Post M&A integration of cloud and hybrid environments deals heavily with overlapping CIDR ranges. Harnessing the synergies of a merger is dependent on the ability to rationalize all these disparate environments into a common transit infrastructure that can then be subject to a common policy and governance model.
The velocity with which this can be achieved without causing any business disruption is a key indicator that defines the success of cloud and networking teams.
The “Layer-3 fits all” approach leads customers down an long and arduous path of post M&A integration that often sacrifices developer productivity and the rollout of new initiatives.
With Prosimo namespaces customers are easily able to carve out overlapping environments, on the same transit infrastructure. With visual transit not only are they able to discover their brownfield connectivity but also are able to make changes (with impact analysis) easily.
For organizations that have Org/BU level allocation of networks by design, namespaces can be used to easily onboard these accounts on the same multi-cloud transit and use policy to connect and secure access.
M&A integration velocity with Prosimo multi-cloud namespaces
Overlapping CIDRs are a common challenge that most networking teams face post M&A or while dealing with partner exchanges. Solving these challenges in a cloud native way, not just relying on legacy appliances is the most pragmatic, cost-effective and future-proof way to unlock value for our customers.
Learn how you can rev up your cloud RPM with Prosimo.
Stop paying for multi-cloud networking
MCN
Foundation
The onramp to Prosimo’s Full Stack Cloud Networking platform.