Adaptive Cloud Network Security
Applications delivered in the cloud face sophisticated cyber threats upon a uniquely dynamic landscape. With cloud’s agility, coupled with the evolving surface area of modern, distributed applications, maintaining a tight security posture is increasingly complex and operationally expensive.
Sophisticated Architecture > Cloud Networking Challenges > Adaptive Cloud Network Security
Applications delivered in the cloud face sophisticated cyber threats upon a uniquely dynamic landscape. With cloud’s agility, coupled with the evolving surface area of modern, distributed applications, maintaining a tight security posture is increasingly complex and operationally expensive. Organizations leveraging security virtual appliances to secure cloud resources often find themselves hindered by rigid operating patterns that slow business execution and spiraling costs to meet throughput demands.
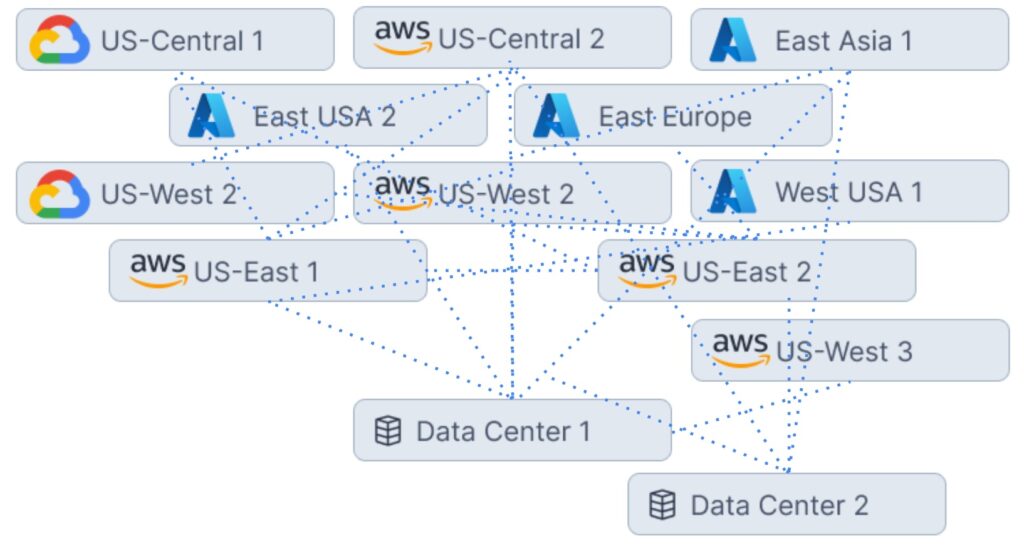
Security Requirements for the Agile Cloud Era
Securing cloud-native platforms, services, and resources requires a vastly different approach to the traditional castle-and-moat security model that followed many enterprises to the cloud. With cloud, perimeters of communication are no longer rigid, shared services across distributed applications are commonplace, and practices like continuous delivery and production A/B testing make for fluid boundaries.
The first phase of cloud adoption saw cloud as a resource extension to systems in private data centers. Application architecture scarcely differed from that of on-premises – the three-tier app architecture of database, middle-ware, and front-end still reigned – and with it the traditional castle-and-moat security model sufficed. At this stage, operating at scale was not of wide-spread concern and many deployed highly-available pairs of virtual security appliances in each VPC/VNET.
With its rapid expansion of platform and service offerings, the second phase of cloud adoption saw a sharp increase in production workloads running entirely in the cloud, with cloud now perceived as a peer to on-premises data centers. A peer in terms of focus and priority, but not necessarily in implementation patterns. Microservice architecture was gaining popularity but security architecture largely still focused on the platform ingress.
The third phase of cloud adoption positions the cloud as the center of gravity with many organizations adopting a cloud-first approach. Application diversity is widespread with architects leaning in on distributed platforms and services spanning both regions and providers. Communication paths are far from linear and the surface area in need of securing is agile – comparatively chaotic to previous phases.
Challenges revealing security posture weakness
Considering the three phases of cloud adoption, and the security architecture implications of each, organizations are typically presented with the following challenges and the individual challenges they represent:
- Growing cost of security appliance sprawl
- Traditional operating practices stalling modern continuous deployment patterns
- Need for intelligent application traffic steering to tighten security while reducing footprint
1. Growing cost of security appliance sprawl
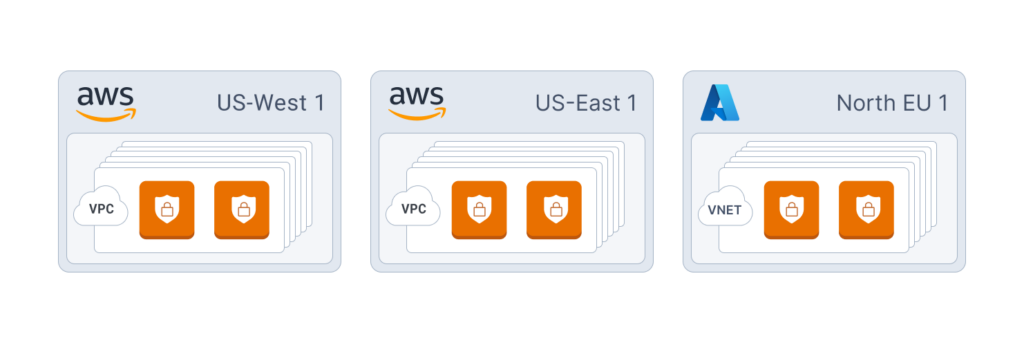
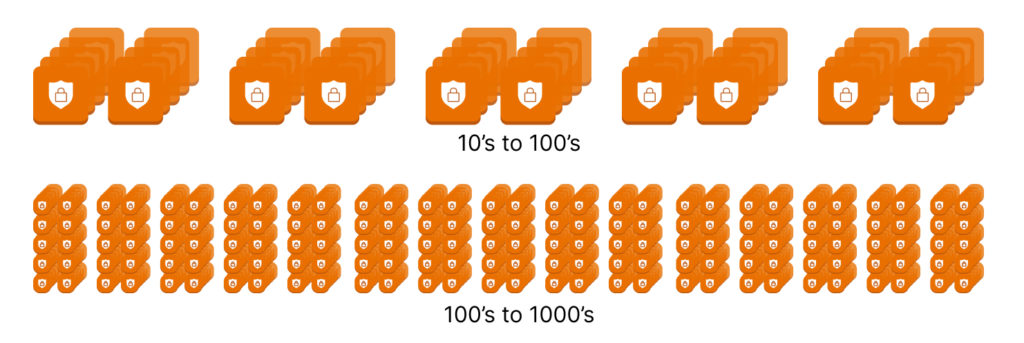
Deploying virtual appliances per VPC/VNET becomes increasingly expensive as adoption grows from 10’s of VPCs / VNETs to 100’s. The combination of compute cost and virtual appliance licensing climbs and, with it, new operational challenges at scale.
2. Traditional operating practices
At phase 2, with accelerated cloud adoption, the increase in scale presents operational challenges that begin to stall execution and competitive edge, for example:
- keeping on top of virtual appliance lifecycle tasks such as upgrades and patching
- ongoing policy management across a highly distributed fleet in the face of continuous deployment practices; or as the network and security appliance operators see it, Continuous Re-Configuration
Appliance vendors responded to the operational challenges with fleet management tools delivering orchestrated patching and upgrades, auditing capabilities, and central configuration management. This era also saw the transition to shared service implementations, with pooled fleets of virtual appliances, and a migration away from the per-VPC/VNET model, whereby application traffic is routed through load-balanced pools presented as a security service. While significantly reducing an organization’s operational cost of their security footprint, two new challenges were presented:
- How to ensure that all traffic is routed to the shared service pool, and;
- Scaling the shared service pool cost effectively
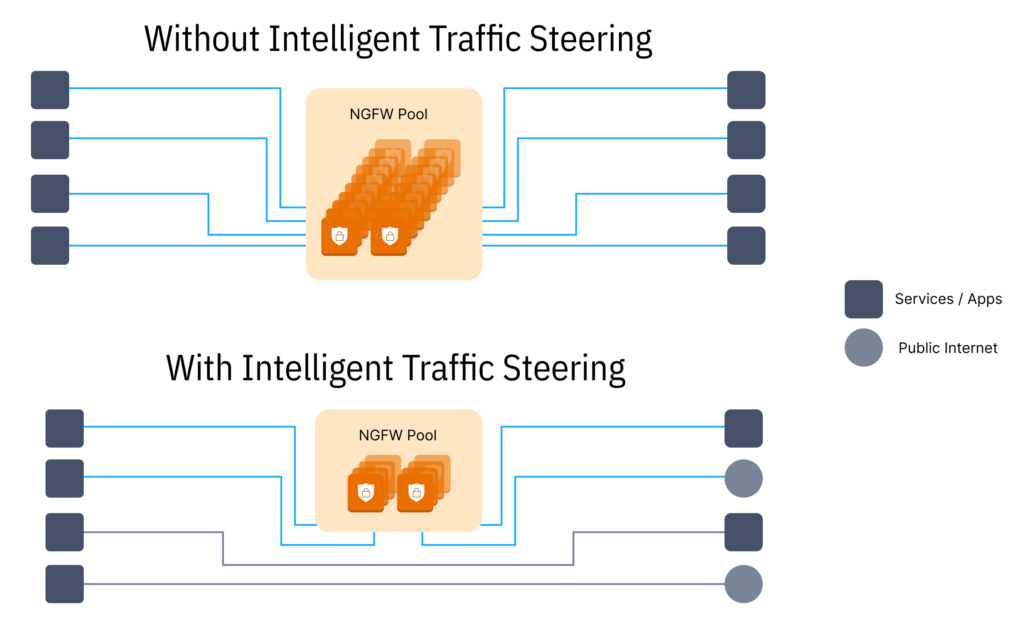
3. Intelligent traffic steering for appliance consolidation
At phases 2 and/or 3 of cloud adoption organizations often realize two new truths about running a shared pool of virtual security appliances:
- routing every session through the shared security fleet is both extremely expensive and unnecessary, however;
- without advanced and precise application traffic control, and the observability to do so without risk, it is required to accept those costs
The following section looks at the technical challenges organizations face when attempting to address these scenarios.
A Sophisticated Approach
Cloud Networking vendors early to cloud, back when cloud-native offerings were scarce and limited in capability, created network overlay solutions focused on layer 3 (IP to IP, subnet to subnet) communication, which worked for phase 1 of cloud adoption with traditional app architecture, but those solutions fell short for the platform and service diversity that came with phases 2 & 3. Networking with application centricity is required to leverage modern cloud capabilities, and the ability to define adaptive cloud network security policies.
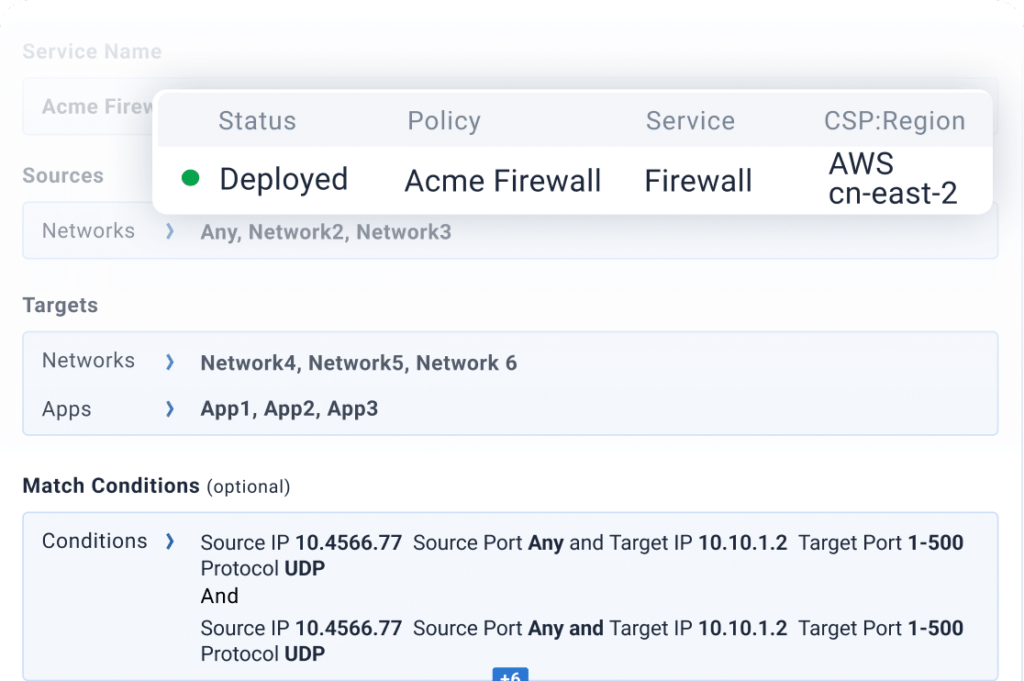
Prisimo’s Adaptive Service Insertion simplifies compliance in the cloud by allowing fine-grained policy definition and real-time visibility to insert stateful services such as firewalls in the path for networks and apps. This reduces the risk of human error, simplifies ongoing maintenance, and helps right-size the services to save costs.
Define adaptive security service insertion policy once and apply to application network paths to:
- Increase control across a diverse and distributed application surface area
- Reduce costs through traffic steering precision and avoid bloated one-size-fits-all scaling
Typical requirements for Cloud Security
Virtual Security Appliance Cost Control:
Deploying virtual appliances per VPC/VNET becomes increasingly expensive as adoption grows from 10’s of VPCs / VNETs to 100’s.
Agile Operating Patterns:
the increase in scale presents operational challenges that begin to stall execution and competitive edge
Intelligent Application Traffic Steering:
Costs skyrocket without advanced and precise application traffic control, and the observability to do so without risk.
OFFICE HOURS
Adaptive Cloud Network Security
Join this live Office Hours session to learn how an Adaptive Cloud Network Security implementation reduces cost, increases agility, and drives towards a tighter security posture.
Speakers

Dan Sheldon

Sharol Pereira