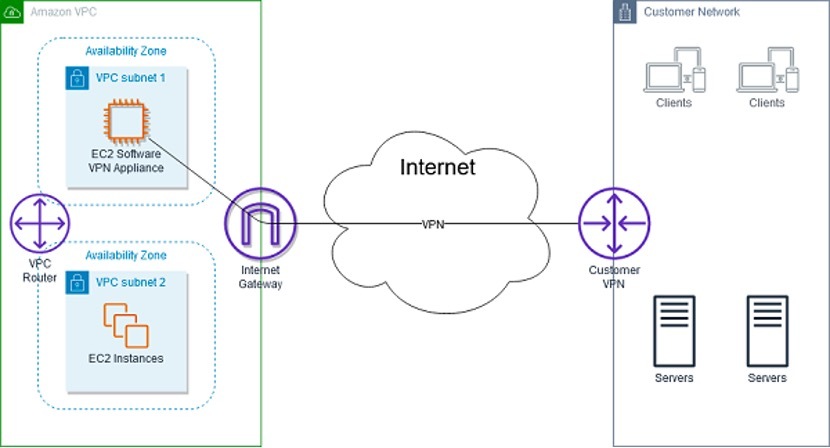
As organizations strive to make their business-critical applications accessible to business partners, they often grapple with secure connectivity and privacy issues. Network routing constructs, such as using AWS Transit Gateways, Layer 3 virtual routers, hub & spoke architectures, or VPC peering, makes it extremely complex to extend enterprise applications such as financial tools, database access, and Platform as a Service (PaaS) to business partners due to a variety of inherent gaps like IP address overlap, route table limits, throughput requirements, route propagation, day-2 operational challenges for TGW and permission related issues for partner cloud subscriptions. Furthermore, these resources are frequently made available via VPN to maintain security with business partners or over the Internet to avoid VPN connectivity issues with IP/Source whitelisting that inadvertently create security vulnerabilities and lead to performance bottlenecks. As such, the prevailing approach to connectivity can result in potential ‘security potholes’ and disrupt the smooth operation of a business.
AWS PrivateLink offers secure and private connectivity between Virtual Private Cloud (VPC) resources and various AWS services. Some commonly used services include S3 storage, RDS, DynamoDB, EFS, and Fargate. Using AWS PrivateLink, enterprises can better meet regulatory requirements that require private network connections for specific data types or workloads. In addition to a range of security advantages, AWS PrivateLink significantly simplifies inter-business collaborations by providing private access to VPC resources, which may encompass financial assets, wealth management tools, databases, etc. Organizations can leverage AWS PrivateLink to establish a private network link connectivity between their respective VPCs and their partners, enabling the private sharing of resources and data. Consequently, the assurance of data security and confidentiality is heightened, reducing the risk of data breaches and other security vulnerabilities.
In this blog, I will take a closer look at how AWS PrivateLink can help solve connectivity challenges for business partners that require access to native AWS services and enterprise assets and what are some of the operational gaps that typically enterprises run into and solve through Prosimo’s Full Stack Cloud-native Transit platform.
AWS Private Link
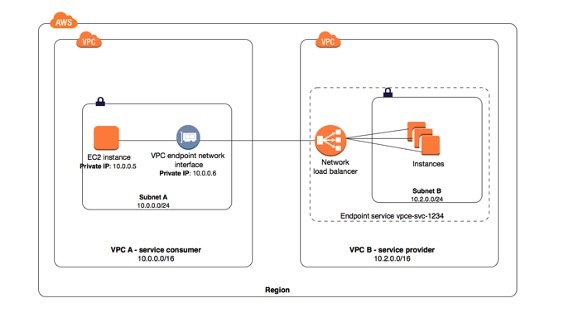
AWS PrivateLink provides reliable, encrypted, fast connectivity between resources in client-managed AWS VPCs, without traversing a public connection. Additionally, the use of AWS PrivateLink eliminates the risk of IP address conflicts between networks on either side of the connection. More technical details on AWS Private Link are found here.
Benefits of using AWS PrivateLink
- Enhanced Security – With AWS PrivateLink, you can access AWS services and third-party services privately without going over the Internet, ensuring that your data remains secure and reducing the risk of data breaches, unauthorized access, and other cyber threats.
- Reduced Latency – Since the traffic stays within the AWS network and never goes over the public internet, AWS PrivateLink reduces latency, resulting in faster access to AWS services over high bandwidth limits.
- Cost-Effective – AWS PrivateLink eliminates the need for costly VPN connections or Network Address Translation (NAT) gateways, reducing overall costs for accessing AWS services.
- Data exchanged over AWS PrivateLink is encrypted.
- Compliance – AWS PrivateLink can help you comply with regulatory requirements that mandate private network connections for certain types of data or workloads
Enabling Seamless Access to Fortune 500 Enterprise Cloud Applications for Business Partners with Prosimo and AWS PrivateLink
I recently got an opportunity to work with an enterprise where the core use case was to allow third-party trusted partner access to sensitive data and critical business applications. These included allowing partners to connect with financial apps, wealth management portals, RDS, and S3 Storage. In the first few architecture sessions, we discovered a few critical operational gaps with traditional IP layer networking that were left to be resolved by customers in making their core service available to business partners;
- Making Target Services (RDS, S3, EC2/Lambda) available to business partners with cross-AWS accounts in different regions
- Source apps and networks in partners’ AWS accounts that need private connectivity to enterprise financial apps, for example, wealth management portals and other banking systems
- Conflicting or Overlapping IP ranges. You can control what you own but not what your partners use as their IP scheme.
- Non-AWS (Azure, GCP, and others) require connectivity to the same services and apps in AWS.
- Little to no visibility and security control to who has access to what.
To increase time to value, the enterprise deployed an architecture using traditional IP layer connectivity approaches in the cloud, including:
- VPN between the enterprise assets in AWS and the business partner cloud workloads using IP layer solutions available from the marketplace using virtual routers.
- Making the apps publicly available and whitelisting IP addresses with all the heavy lifting of managing SG ACLs to allow/deny business partners.
The initial implementation functioned satisfactorily as an MVP for a select group of partners. However, as the range of their services expanded, the operational management became increasingly challenging. This included basic tasks such as IP/Source whitelisting for partners and adding them in SG ACLs, route table management, route propagation, and the addition or deletion of route entries. Other challenges involved dealing with restrictions and bottlenecks regarding throughput, the number of route entries, and ensuring the VPN remains operational and in compliance with various regulations and encryption standards. Moreover, managing IP overlap issues introduced additional complexities due to Network Address Translation (NAT). This approach hindered their ability to scale swiftly, launch modern applications for partners in the marketplace, and efficiently handle service tickets to maintain connectivity to existing applications and services
How Prosimo orchestrates AWS Private Link to connect business partners
With Prosimo’s Cloud-native Networking suite, they could use cloud-native peering options depending on the endpoint to attach their workloads and AWS Services; for example, the EC2 instances, networks, and IP endpoints, HTTP and TCP applications are connected using Transit Gateway attachments and AWS Services (S3, RDS, Dynamo DB, Fargate, etc.) are attached using Private Link endpoints. The benefit of this approach is to treat every endpoint uniquely. Prosimo provided them with an orchestration and abstraction suite using a SaaS control plane to provision TGW, VPC attachments to TGW, Route table management, route propagation, Private Link endpoint services, and SG ACL orchestration, to name a few with a simple click-n-go wizard model that works across different cloud platforms. The abstraction layer hides the complexity of configuring different networking constructs manually or through automation.
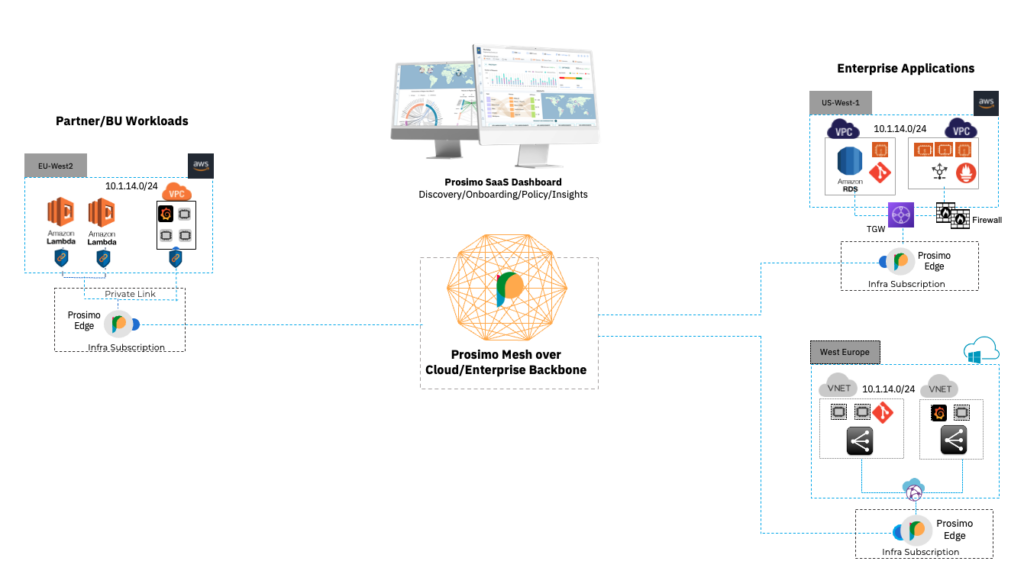
Extending Private Link across regions using Prosimo Full Stack
In this example, Prosimo Edge gateways in US-West-2 and US-West-1 are connected over the AWS backbone to form a cloud-native mesh between two regions, and endpoints (EC2 and services) are attached to the regional Edge gateways, respectively, using Private Link endpoint and TGW. Considering AWS Private Link is a regional construct, enterprises can take advantage of cloud-native created using Prosimo edges to extend Private Link to multi-region
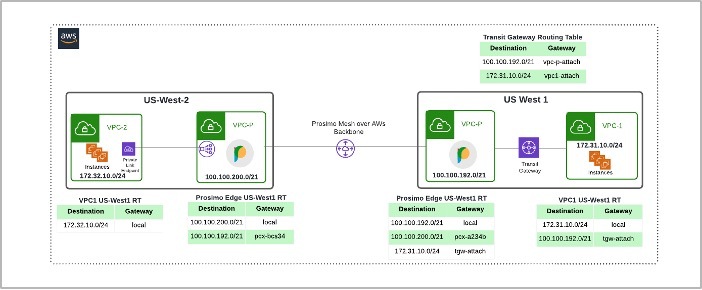
Extending AWS Services (PaaS, EC2, and enterprise apps) across Multi-Cloud
The same Cloud-native mesh can be built over a Public Internet or Private backbone between two cloud providers (AWS – Azure or GCP) to extend connectivity and services to business partners not using AWS as their primary cloud.
Prosimo mesh is underlay agnostic and can be over the Internet or private backbone where the end-to-end path is encrypted using mTLS and tunneling encapsulation.
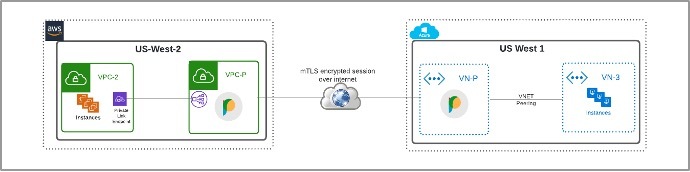
Using Private Link to remove Overlapping IP address challenges
Prosimo also enables enterprises with overlapping IP address challenges using PrivateLink endpoint at source VPCs attached to Prosimo Edge hosted in enterprise AWS account and acts as a hub that routes traffic between the VPC endpoints. When a client requests a resource from an AWS service, the request is sent to the VPC endpoint in the client’s or source VPC. The VPC endpoint sends the request to the Prosimo Edge VPC, which routes the request to the appropriate AWS service. The response is then sent back to the Prosimo VPC, which routes it back to the VPC endpoint in the client’s VPC. Prosimo allows enterprises to use AWS PrivateLink with overlapping IP address ranges while maintaining security and compliance. It also provides a centralized and streamlined way to manage networking resources, reducing complexity and improving scalability.
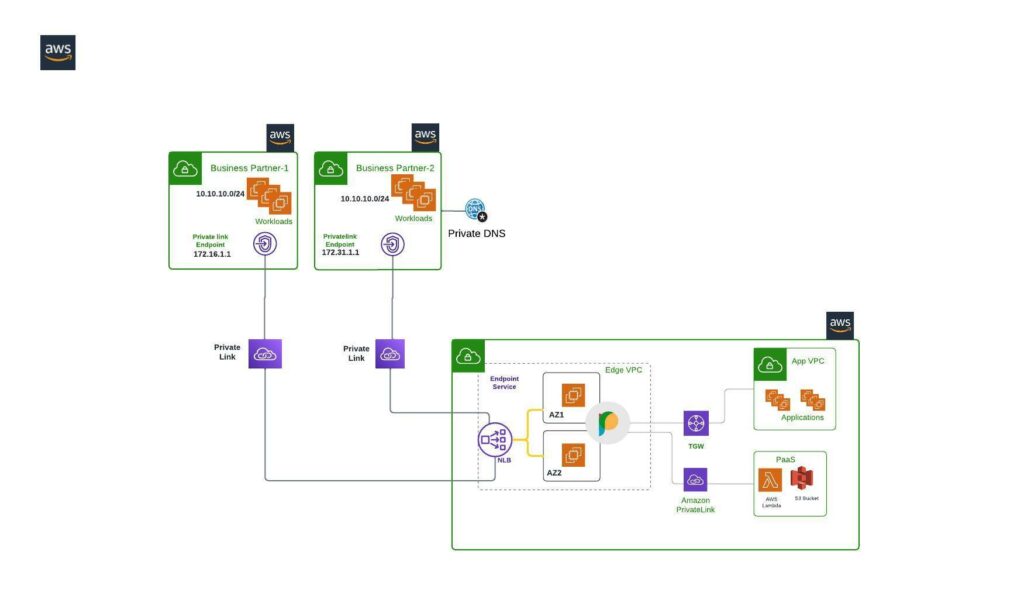
Steps to Configure Private Link using Prosimo with Overlapping IP addresses
In this section, I will walk you through the steps to connect applications in Partner Cloud Accounts to Enterprise workloads using AWS Private Link, fully orchestrated through the Prosimo Cloud-Native Transit platform.
You can configure the Private Sources in Prosimo with overlapping IP addresses, which provisions the Private link endpoint using the cloud permissions in partners’ AWS accounts and utilize Prosimo Edge gateways to connect to resources running in the AWS enterprise account with connectivity policies to govern and isolate partners using application FQDNs, Network objects, namespaces, and Network groups.
You can configure the Private Sources in Prosimo with overlapping IP addresses, which provisions the Private link endpoint using the cloud permissions in partners’ AWS accounts and utilize Prosimo Edge gateways to connect to resources running in the AWS enterprise account with connectivity policies to govern and isolate partners using application FQDNs, Network objects, namespaces, and Network groups.
In conclusion, Prosimo, utilizes cloud-native tools like AWS’s PrivateLink (or GCP’s Private Service Connect) to facilitate the connection of business partners’ workloads with enterprise applications. It also enables access to other services AWS and PaaS provide in the marketplace, thus supporting critical business functions. If you want to give it a try – See more features to that help you build cloud networking for the future.
