TL;DR: “On 30 September 2025, default outbound access connectivity for virtual machines in Azure will be retired.” Read more about the Azure changes here.
Introduction
Azure is transitioning its VM outbound access defaults, a significant change that could impact many users. This blog post delves into the challenges posed by this transition and how Prosimo offers effective solutions to prep for these changes
Windows Activation & Updates
- VMs in Azure depend on public connectivity for essential functions like activation and updates. The new Azure defaults could disrupt these critical processes, leading to potential system vulnerabilities and performance issues.
Dependency Failures
- Many systems interface with other systems, public APIs, and various endpoints. Restricting outbound access can lead to failures in these dependencies, disrupting operations and data flow.
Increasing Complexity
- Introducing elements like NAT Gateways, route tables, and routes to manage new outbound access rules can significantly complicate network setups. This complexity can lead to increased administrative overhead and potential for errors.
Review Imperative
- With Azure’s changes, it’s crucial to review deployment pipelines and applications to ensure they maintain uninterrupted Internet access. This review process is vital to avoid unexpected disruptions in service.
Common Approaches and Challenges
A typical response might involve directing traffic through regional firewalls. However, the dynamic nature of cloud environments makes this a challenging task, especially for network and security teams that are already under considerable strain.
How Prosimo helps to navigate around these changes in a few months.
Prosimo offers innovative solutions to address these challenges:
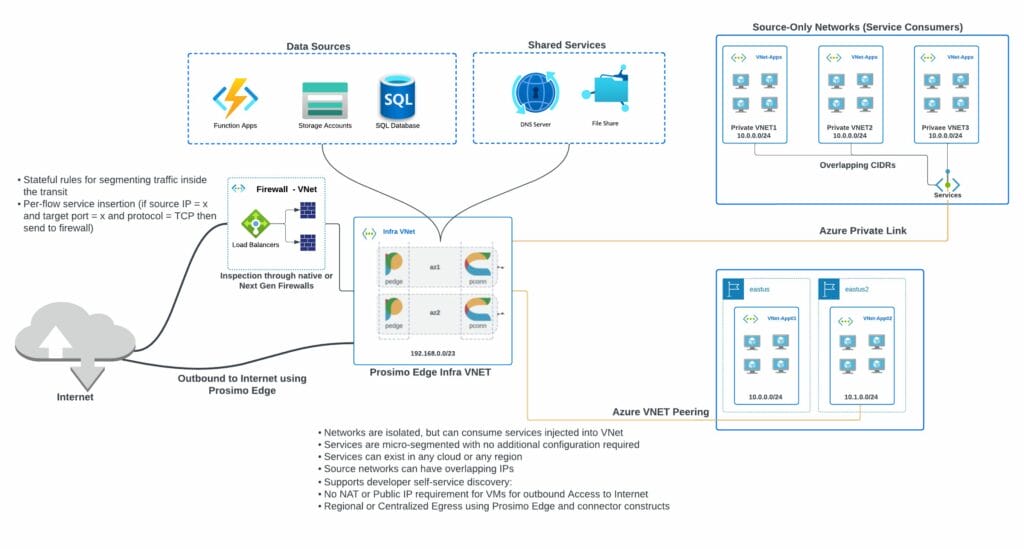
Default Internet Route via Prosimo:
- Eliminate the need for public IPs on your VMs. Direct internet access from your private subnets through Prosimo for Egress, and manage remote user access via Prosimo Private Proxy for ingress when needed.
Spoke-less Architecture with Private Link:
- Simplify your network architecture while maintaining secure and private connectivity.
Per-flow Service Insertion:
- Gain granular control over your network flows, enhancing security and efficiency.
Route Orchestration and Management:
- Simplify the management of your network routes, reducing complexity and administrative burden.
Conclusion
The upcoming Azure shift in VM outbound access defaults is a significant change, but it doesn’t have to disrupt your operations. You can navigate this transition smoothly by understanding the challenges and equipping yourself with the right tools and strategies, such as those offered by Prosimo. Reach out now to see how Prosimo can assist in adapting to these changes.
